CBSE Sample Papers for Class 12 Computer Science Paper 3 is part of CBSE Sample Papers for Class 12 Computer Science. Here we have given CBSE Sample Papers for Class 12 Computer Science Paper 3.
CBSE Sample Papers for Class 12 Computer Science Paper 3
| Board | CBSE |
| Class | XII |
| Subject | Computer Science |
| Sample Paper Set | Paper 3 |
| Category | CBSE Sample Papers |
Students who are going to appear for CBSE Class 12 Examinations are advised to practice the CBSE sample papers given here which is designed as per the latest Syllabus and marking scheme, as prescribed by the CBSE, is given here. Paper 3 of Solved CBSE Sample Paper for Class 12 Computer Science is given below with free PDF download Answers.
Time: 3 Hours
Maximum Marks: 70
General Instructions
- All questions are compulsory within each Section.
- Programming Language in SECTION A : C++.
- Answer the questions after carefully reading the text.
SECTION A
Question 1.
(a) Which of the following array declarations are invalid?
(i) float value [20];
(ii) int result [10];
(iii) float x [+30];
(iv) account [10] of float
(b) Sahil has started learning C++ language and has typed the following program. When he compiled the following code, he discovered that he needs to include some header files to successfully compile and execute the code. Write the names of those header files, which are required to be included in the code.
void main()
{
char Text[]="paper";
cout<<setw(15)<<Text;
}
(c) Rewrite the following program after removing the syntactical error(s), if any. Underline each correction.
Note: Assume all required header files are already being included in the program.
void main()
{
First=10, Second=20;
Show(First; Second);
Show(Second);
}
void Show(int N1, int N2=20)
{
N1=N1+N2;
cout<>N2;
}
(d) Find and write the output of the following C++ program segment:
Note: Assume all required header files are already being included in the program.
void display()
{
char *Name[2]={"COMPUTER", "SCIENCE"};
for(int a=0; a<2; a++)
{
for(int b=0; b<strlen(Name[0]); b++)
if(islower(Name[a][b]))
cout<<(char)toupper(Name[a][b]);
else if (isupper (Name [a] [b] )&&(b%2==0))
cout<<(char)tolowed Name[a][b]);
else
cout<<Name[a][b];
cout<<b< }
}
(e) Give the output of the following C++ program code:
Note: Assume all required header files are already being included in the program.
class Exam
{
int Level, Marks;
char Subject;
public:
Exam(char ESubject='M')
{
Level=1;
Marks=96;
Subject=ESubject;
}
void Teacher(int T);
void Chang();
void Display()
{
cout<<Subject<<"@"<< cout<<Marks;
}
};
void main()
{
Exam A('s'), B;
B.Display();
A.Teacher(2);
A.Change();
B.Teacher(3) ;
A.Display();
B.Display();
}
void Exam::Change()
{
Subject=(Subject=='M')? 'S':'M’ ;
}
void Exam::Teacher(int T)
{
Marks+ = T;
if(Marks>=30)
Level=3;
else if(Marks>=20)
Level=2;
else
Level=1;
}
(f) In the following program, find the correct possible output(s) from the options (i) to (iv) following it. Also, write the minimum and maximum values that can be assigned to the variable f.
Note: Assume all required header files are already being included in the program.
random(n) function generates an integer between 0 to n-1
void main()
{
randomize();
char City[][10]={"MEE","BNG", "DEL", "KOL", "BOM"};
int f;
for(int a=0; a<3; a++)
{
f=random(2)+1;
cout<<City[f]<<":";
}
}
Output
(i) MEE:BNG:DEL:
(ii) BNG:DEL:BNG:
(iii) DEL:KOL:BOM:
(iv) DEL:BNG:DEL:
Question 2.
(a) Differentiate between public and private visibility modes in the context of Object Oriented Programming using a suitable example to illustrate each.
(b) Answer the following questions (i) and (ii) after going through the following program.
Note: Assume all necessary header files are already being included in the program.
class Market
{
char Name[20];
char Address[20];
int noofshops;
float Price:
Market() // Function1
{
strcpy(Name, "CWK");
strcpy(Address, "Delhi"):
noofshops=20;
Price=50000;
}
public:
void Show() // Function2
{
cout<<Name<<"-"<<Address<<":"<<noofshops<<"@"<<Price;
}
};
void main()
{
Market M; // Statement1
M.Show(); 7/ Statement2
}
(i) Will Statement1 initialize all the data members for object M with the values given in theFunctiona1l? (Yes or No). Justify your answer suggesting the correction(s) to be made in the above code.
(ii) In Object Oriented Programming, what is Function1 referred as and when does it get invoked/called?
(c) Define a class LCD in C++ with the following description:
Private members
- Model_No of type integer
- Manufacturer of type string
- Cost of type integer
- Sold (number of LCD sold) of type integer
- Sale_Amt of type double
- A member function CALCULATE ()
To calculate and return the total amount of sales (Sold*Cost)
Public members
- A function INPUT() to allow a user to enter values for Model_No, Manufacturer, Cost and Sold and call function CALCULATE () to assign the
Sale_Amt. - A function DISPLAY() to allow a user to view the content of all the data members.
(d) Answer the questions (i) to (iv) based on the following:
class Normal
{
char Ccode[10];
public:
void Input();
void Output();
};
class Live
{
char Wcode[50];
public:
void LIn();
void LOut();
};
class Teacher: public Normal, private Live
{
long Tcode;
float Fees;
int Time:
public:
void Register();
void Show();
};
(i) Which type of inheritance is shown in the above example?
(ii) Write names of all the member functions accessible from Show() function of class Teacher.
(iii) Write names of all the member functions accessible through an object of class Teacher.
(iv) Write the names of all data members which are accessible by class Live.
Question 3.
(a) Write a function Modify() in C++, which accepts an array of integer and its size as parameters and divide all those array elements by 5, which are divisible by 5 and multiple other array elements by 4.
e.g. If the array contains
10, 12, 6, 35, 8
Output will be
2, 48, 24, 7, 32
(b) An array A [20] [10] is stored in the memory along with the column with each element occupying 2 bytes. Find out the address of the element A[3] [5], if the base address is 100.
(c) Write a function in C++ which accepts a 2D array of integers and its size as arguments and displays the elements of the middle row and the elements of the middle column. [Assuming the 2D array to be a square matrix with odd dimension, i.e. 3 x 3, 5 x 5, 7 x 7 etc.]
e.g. if the array content is
2 4 5
7 3 9
3 2 5
Output through the function is
Middle Row: 7 3 9
Middle Column: 4 3 2
(d) Write infix expression for the following postfix expression. Show the status of the stack after execution of each operation.
p q AND p r AND OR
(e) Consider the following portion of a program, which implements passengers queue for a flight. Write the definition of function Insert (whose prototype is shown below) to insert a new node in the queue with the required information.
struct NODE
{
long Ticketno;
char PName[20];
NODE *NEXT;
};
class Queueofflight
{
NODE *Rear,*Front;
public:
Queueofflight()
{
Rear=NULL;
Front=NULL;
}
void Insert():
void Delete():
~Queueofflight();
};
Question 4.
(a) Observe the following code carefully and considering that the binary file “stu.dat” exists on disk. Find the output of the following C++ program:
#include<iostream.h>
#include<conio.h>
#include<fstream.h>
#include<stdio.h>
class Student
{
int roll;
char name[20];
float marks;
void main()
{
fstream f;
f.open("stu.dat", ios::binary | ios::in);
Student s1;
int pos;
f. read((char*)&s1, sizeof(s1));
f.read((char*)&s1, sizeof(s1));
pos=f.tellg();
f.read((char*)&s1, sizeof(s1));
f.read((char*)&s1, sizeof(s1));
cout<<"tellg:"<<f.tellg()<<endl;
f.seekg(pos);
cout<<"tellg:"<<f.tellg();
f.close();
getch();
}
(b) Write a function in C++ to count and display the number of lines not starting with alphabet ‘A’ present in a text file “STORY.TXT’.
e.g. If the file “STORY.TXT’ contains the following lines:
A rose is red.
A girl is playing there.
There is a playground.
An airplane is in the sky.
Numbers are not allowed in the password.
The function should display the output as 2.
(c) Given a binary file EMPLOYEE.DAT, containing records of the following class Employee type:
class Employee
{
char ECode[10]; // Identity code of employee
char *EName; // Name of employee
int Salary;
public:
void EnterData()
{
gets(ECode);
gets(EName);
cin>>Salary;
}
void DisplayData()
{
cout<<setw(12)<<ECode;
cout<<setw(32)<<EName;
cout<<setw(3)<<Salary<<endl;
}
char *ReturnName()
{
return EName;
}
};
Write a function in C++ that would read contents from the file EMPLOYEE.DAT and creates a file named RECORD.DAT copying only those records from EMPLOYEE.DAT where the employee name is “John”.
SECTION B
Question 5.
(a) Consider the tables DOCTORS and PATIENTS given below:

Answer the following questions:
(i) Write the primary key of both the tables.
(ii) Write the Cardinality of both tables.
(b) Write SQL queries for (i) to (iv) and find outputs for SQL queries (v) to (viii), which are based on the tables.

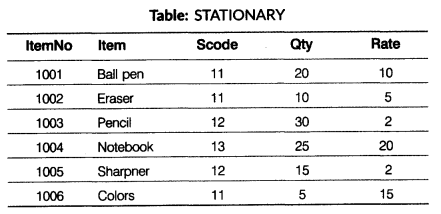
(i) To display detail of all the items in the table STATIONARY in ascending order of Qty.
(ii) To display ItemNo, Item name of those items from table STATIONARY whose Rate is more than ₹ 15.
(iii) To display detail of those items whose supplier code (SCode) is 12 or quantity (Qty) in stationery is more than 10 from the table STATIONARY.
(iv) To display the minimum Rate of items for each supplier individually as per Score from the table STATIONARY.
(v) SELECT COUNT(DISTINCT Scode) FROM STATIONARY; (vi) SELECT Rate*Qty FROM STATIONARY WHERE ItemNo = 1001; (vii) SELECT Item, Sname FROM STATIONARY S, SUPPLIERS U WHERE S.Scode=U.Scode AND ItemNo=1006; (viii) SELECT Item, ItemNo, Rate, Sname FROM STATIONARY, SUPPLIERS WHERE STATIONARY.Scode=SUPPLIERS.Scode AND Qty<14;
Question 6.
(a) State and verify Associative law algebraically.
(b) Implement the following expression using NAND logic:
\(F=\left( \bar { A } \bar { B } +CD \right)\)
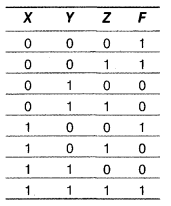
(c) Write the Sum of Product (SOP) form of the function F(X, Y, Z) for the following truth table representation of F:
(d) Obtain a simplified form for the Boolean expression using K-map.
F (a, b, c, d) = Σ (0, 2, 5, 7, 8, 10, 11, 13, 15)
Question 7.
(a) Write the difference between co-axial cable and optical cable.
(b) What is the purpose of an application gateway?
(c) While designing networks, what factor related to performance, would you consider?
(d) Write two advantages of using an optical fiber cable over an Ethernet cable to connect two service stations, which are 200 m away from each other.
(e) Lastec corporation caters to many high profile clients and has 5 buildings where it runs its operations.
Note: [ ] represents the number of computers.
\(\underleftrightarrow { Number }\) represents the distance between two buildings.

Answer the following questions on the basis of above-given information:
(i) Suggest the possible cable layout for the buildings.
(ii) Where would you suggest the placement of the server?
(iii) Suggest the cable type that should be used.
(iv) The management wants that the network traffic should be minimized. For this which network device would you suggest out of the following devices and why?
I. Hub
II. Repeater
III. Bridge
(f) What is the difference between HTTP and FTP?
(g) How are viruses harmful?
Answers
Answer 1.
(a) (iii) and (iv) are invalid array declarations.
(b) → cout()
→ setw()
(c) void Show(int N1, int N2=20):
void main()
{
int First=10, Second=20;
Show(First, Second);
Show(Second);
}
void Show(int N1, int N2)
{
N1 = N1+N2;
cout<<N1<<N2;
}
(d) Output
cOmPuTeR 8
sCiEnCe 8
(e) Output
M@1
96M@3
98M@3
99
(f) The possible output will be
(ii) BNG:DEL:BNG: and (iv) DEL:BNG:DEL:
The minimum value of f = 1
The maximum value of f = 2
Answer 2.
(a) Differences between public and private visibility modes are as follows:
| Private visibility mode | Public visibility mode |
| A member declared as private remains hidden from the outside world. | A member declared as the public is made available to the outside world. |
| It can only be accessed by the member functions of that class. | It can be accessed by any function or expression in the program but only by using an object of the same class type. |
These access labels enforce data hiding and abstraction.
e.g.
#include<iostream.h>
class Illustrate
{
private: int i;
public:
int j;
void access()
{
i=10; //Accessing private data member
cout<<i<<endl:
}
};
void main()
{
II1ustrate obj;
obj.i=20;
/* Error! private members cannot be directly accessed outside the class */
obj.access();
/* Accessing private member indirectly through public member function of the class */
obj.j=20;
cout<<obj.j:
/* The public member of the class can be directly accessed outside the class using class object */
}
(b) (i) No, Statementl will not initialise the data members because the constructor is declared as private and it is not possible to create object outside the class. Thus, to initialise an object the constructor should be declared as public member.
(ii) The Function 1 is referred as constructor and is invoked automatically as soon as the object is allocated memory.
(c) class LCD
{
int Model_No;
char Manufacturer[30];
int Cost, Sold:
double Sale_Amt;
double CALCULATE();
public:
void INPUT();
void DISPLAY():
};
double LCD::CALCULATE()
{
double total;
total = Sold*Cost;
return(total);
}
void LCD::INPUT()
{
cout<<"Enter Model Number"; cin>>Model_No;
cout<<"Enter the Name of Manufacturer";
gets(Manufacturer);
cout<<"Enter Cost"; cin>>Cost;
cout<<"Enter Number of LCD sold "; cin>>Sold;
Sale_Amt = CALCULATE();
}
void LCD::DISPLAY()
{
cout<<"Model Number: "<<Model_No<<endl;
cout<<"Manufacturer Name: "<<Manufacturer<<endl;
cout<<"Cost: "<<Cost<<endl;
cout<<"Number of LCD sold: "<<Sold<<endl;
cout<<"Total Sale Amount: "<<Sale_Amt;
}
(d) (i) Multiple Inheritance
(ii) Register(), L!n(), LOut(), lnput(), Output()
(iii) Register(), Show(), lnput(), Output( )
(iv) Wcode
Answer 3.
(a) void Modify(int A[], int n)
{
for(int i=0; i<n; i++)
{
if(A[i]%5==0)
A[i]=A[i]/5;
else
A[i]=A[i]*4;
}
}
(b) In a column major arrangement, address of particular location [I, J] is
Base address B = 100
Element size W = 2 bytes
Number of row n = 20
Lowerbound of row Ir = 0
Lowerbound of column Ic = 0
Hence, A[I][J] = B + W* [n(J – Ic) + (I – Ir)]
A[3][5] = 100 + 2*[20*(5 – 0) + (3 – 0)]
= 100 + 2*[20 x 5 + 3]
= 100 + 2*[100 + 3]
= 100 + 2*(103)
=100 + 206 = 306
(c) void Middle(int A[][], int R)
{
int M, i;
M = R/2;
cout<<"Middle Row: "<<endl:
for(i = 0; i<R; i++)
cout<<A[M][i]<<" ";
cout<<"\n Middle Column: "<<endl:
for(i=0; i<R; i++)
cout<<A[i][M]<<" ";
}
(d) The given expression is p q AND p r AND OR
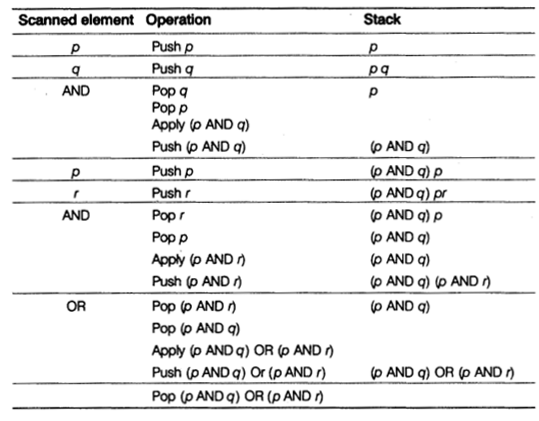
Result = (p AND q) OR (p AND r)
(e) void Insert()
{
NODE *ptr;
ptr=new NODE:
cout<<"Enter ticket Number"<<endl; cin>>pti—>Ticketno;
cout<<"Enter Passenger Name"<<endl; cin>>ptr->PName;
ptr->next=NULL;
if(Front==NULL)
{
Front=Rear=ptr;
}
else
{
Rear->next = ptr;
Rear=ptr;
}
}
Answer 4.
(a) Output
tellg: 104
tellg: 52
(b) void Countline()
{
ifstream filein;
char arr[80];
filein.open("STORY.TXT", ios::in);
if(!filein)
{
cout<<"File does not exist !";
exit(0);
}
int i = 0;
while(!filein.eof())
{
filein.getline(arr, 80);
if(!(arr[0]=='A' || arr[0]=='a'))
i++;
}
filein.close();
cout<<"Total number of lines not starting with alphabet A";
cout<<i<<endl;
}
(c) void readfile()
{
Employee obj; fstream f("EMPLOYEE.DAT", ios::in | ios::binary);
fstream f1("RECORD.DAT", ios::out | ios::binary);
while(f.read((char*)&obj, sizeof(obj)))
{
if(strcmp(obj.ReturnName(), "John") == 0)
f1.write((char*)&obj, sizeof(obj));
}
f.close();
f1.close();
}
Answer 5.
(a) (i) DocID is the primary key for DOCTORS
PatNo is the primary key for PATIENTS
(ii) Cardinality for DOCTORS is 3
Cardinality for PATIENTS is 5
(b) (i) SELECT * FROM STATIONARY ORDER BY Qty; (ii) SELECT ItemNo, Item FROM STATIONARY WHERE Rate >15; (iii) SELECT * FROM STATIONARY WHERE Scode = 12 OR Qty>10; (iv) SELECT MIN(Rate). Scode FROM STATIONARY GROUP BY Scode;

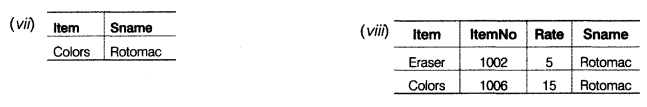
Answer 6.
(a) The Associative law states:
(i) X + (Y + Z) = (X + Y) + Z
(ii) X.(Y.Z) = (X.Y).Z
Verification from truth table
(i) X + (Y + Z) = (X + Y) + Z
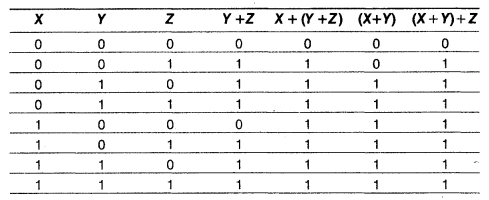
Both the columns (X + (Y + Z)) and ((X + Y) + Z) are identical.
Hence Proved.
(ii) X.(Y.Z) = (X.Y).Z
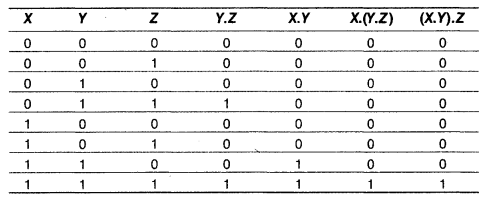
Both the columns(X.(Y.Z)) and ((X.Y).Z) are identical.

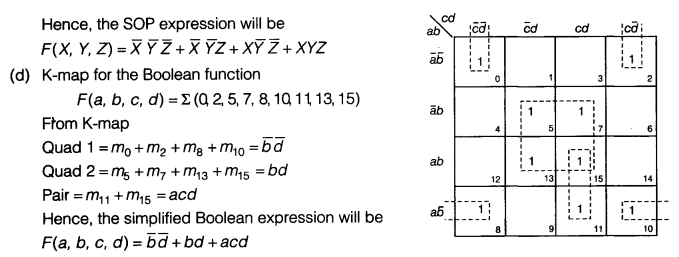
Answer 7.
(a) Differences between co-axial cable and optical cable are as follows:
| Co-axial Cable | Optical Cable |
| Co-axial cable has a solid wire core surrounded by one or more wire shields. | The optical cable consists of thin strands of glass or glass-like materials. |
| Co-axial cables transmit electrical signals. | Optical fibers transmit light signals. |
(b) Application gateway applies security mechanisms to specific applications such as FTP and Telnet servers. This is very effective but can impose a performance degradation.
(c) While designing networks, we would consider network reliability, traffic throughput and host/client computer speeds etc., factors related to performance.
(d) Two advantages of using an optical fiber cable over an Ethernet cable are as follows:
(i) Optical fiber cable guarantees secure transmission and very high transmission capacity.
(ii) Optical fiber cable is immune to electrical and magnetic interference.
(e) (i) Cable Layout

(ii) A server should be placed in building P2 to minimize network traffic as 80% to 20% because it has the maximum number of computers.
(iii) Thicknet co-axial cable as these can support networks of up to 500m long.
(iv) III. A bridge should be used in order to minimize traffic. This is because the bridge identifies the destination segment depending upon the receiver’s MAC address rather than broadcasting the data.
(f) FTP is a protocol used to upload files from a workstation to an FTP server or download files from an FTP server to a workstation whereas, HTTP is a protocol used to transfer files from a Web server onto a browser in order to view a Web page that is on the Internet.
(g) Virus’s main objective is to make your system unstable and cause harm to data. Mainly these cause damage in many ways as follows:
- Can corrupt entire file system.
- Create a bad sector on a disk.
- Decrease the space on the hard disk by duplicating files.
- Alter data in data files.
- Cause the system to hang.
We hope the CBSE Sample Papers for Class 12 Computer Science Paper 3 help you. If you have any query regarding CBSE Sample Papers for Class 12 Computer Science Paper 3, drop a comment below and we will get back to you at the earliest.